| Features | EXT2 Second extended file system | EXT3 Third extended filesystem | EXT4 Fourth extended file system |
|---|---|---|---|
| Developer(s) | Rémy Card | Stephen Tweedie | Mingming Cao, Andreas Dilger, Alex Zhuravlev, others |
| File allocation | bitmap (free space), table (metadata) | bitmap (free space), table (metadata) | Extents/Bitmap |
| Max. volume size | 2–32 TiB | 4 TiB – 32 TiB | 1 EiB |
| Max. file size | 16 GiB – 2 TiB | 16 GiB – 2 TiB | 16 TiB (for 4k block filesystem) |
| Max. number of files | 1018 | Variable, allocated at creation time | 4 billion (specified at filesystem creation time) |
| Max. file name length | 255 bytes | 255 bytes | 255 bytes |
| Allowed characters in file names | All bytes except NUL ('\0') and '/' | All bytes except NUL ('\0') and '/' | All bytes except NUL ('\0') and '/' and the special file names "." and ".." |
| Date range | December 14, 1901 - January 18, 2038 | December 14, 1901 – January 18, 2038 | 14 December 1901 - 25 April 2514 |
| Supported operating systems | Linux, BSD, Windows (through an IFS), Mac OS X | Linux, BSD, Windows (through an IFS) | Linux FreeBSD (read-only with ext4fuse) Mac OS X (read-only with ext4fuse, full with ExtFS) Windows (Read/Write without journaling with ext2fsd) |
Monday, December 21, 2015
Difference between EXT2, EXT3,EXT4
Difference between LVM1 and LVM2
| Features | LVM1 | LVM2 |
|---|---|---|
| RHEL 3 support | YES | NO |
| RHEL 4 support | NO | YES |
| Transactional metadata for fast recovery | NO | YES |
| Shared volume mounts with GFS | NO | YES |
| Cluster Suite failover supported | YES | YES |
| Striped volume expansion | NO | YES |
| Max number PVs | 256 PVs | 2**32 PVs (4294967296) |
| Max number LVs | 256 LVs | 2**32 PVs (4294967296) |
| Max device size | 2 Terabytes | 8 Exabytes (64-bit CPUs) |
| Volume mirroring support | NO | YES |
Sunday, December 13, 2015
AWK Commands for Linux
1: Field/text processor
2: Default Field-delimiter is white-space.
3: Stores fields (columns) into tokens, which then become accessible during processing
4: Will accept input from: file or STDIN or pipe
Commands:
1: To print each line in its entirety.
2: Default Field-delimiter is white-space.
3: Stores fields (columns) into tokens, which then become accessible during processing
4: Will accept input from: file or STDIN or pipe
Commands:
1: To print each line in its entirety.
# awk '{ print $0 }' test.txt2: To print column #1 from each line.
# awk '{print $1}' test.txt3: To print column #2 from each line.
# awk '{print $2}' test.txt4: To print column #1 then #2.
# awk'{print $2,$1}' test.txt5: To print all columns where line includes 'Red'.
# awk'/Red/ {print $0}' test.txt6: To print column #1,#2,#3 where line include 'Red'.
# awk '/Red/ {print $1, "-",$2,"-",$3}' test.txt7: To print all columns of records containing '2012' in the second column.
# awk '{if ($2 ~ /2012/) print $0}' test.txt8: To print lines ending in : 2012.
# awk '/2012$/ {print $0}' test.txt9: Accept a pipe using above point 8 commands.
# grep 2012 /var/log/messages | awk '/2012/ {print $0}'10: To print columns $3-$6 where column 2 = '9'.
# awk '{if ($2 ~ /9/) print $3,$4,$5,$6}' /var/log/message
Wednesday, December 9, 2015
Most useful find commands for Linux SystemAdmin.
1 : Search the file aaa from current directory downwards and print it.
2 : Find all files which begin with 'a' or 'b' from current directory.
3 : Search directories called backup from /usr directory.
4 : Search normal files called backup from /usr directory.
5 : Search character special files called backup from /usr directory.
6 : Search block special files called backup from /usr directory
7 : Search all directories from /usr whose inode number is 1235 and print them.
8 : Search in root directory for all files which have less than 2 links.
9 : Search in current directory for all files whose owner is abc1 and group is grp1.
10 : Search in current directory for all files whose owner is abc1 or whose name is myfile1.
11 : Search in current directory for all files which have permissions 777.
12 : Search in current directory for all files chose size is 10 blocks.
13 : Search in current directory for all files whose size 10 bytes(characters).
14 : Search in current directory for all files whose size is greater than 10 byets.
15 : Search in current directory for all files which were accessed exactly 7 days back.
16 : Search in current directory for all files which have not been accessed since last 7 days (or in other words which were accessed more than 7 days ago.)
17 : Search in current directory for all files which have not been modified since last 7 days (or in other words which have been modified more than 7 days ago.)
18 : Search in current directory for all files whose status has changed (on creation or modification ) more than 7 days ago.
19 : Search in current directory for all files whose name is cog and instead of printing their names executes a command rm on the searched files.
Here, the {} indicate that the searched files would become arguments for rm.The semicolon is necessary and it has to be preceded by a \ to take away its special meaning.
20 : Same as above except that this time it should ask for confirmation before executing rm command.
# find . -name aaa - print
2 : Find all files which begin with 'a' or 'b' from current directory.
# find . -name [ab]* -print
3 : Search directories called backup from /usr directory.
# find /usr -type d -name backup -print
4 : Search normal files called backup from /usr directory.
# find /usr -type f -name backup -print
5 : Search character special files called backup from /usr directory.
# find /usr -type c -name backup -print
6 : Search block special files called backup from /usr directory
# find /usr -type b -name backup -print
7 : Search all directories from /usr whose inode number is 1235 and print them.
# find /usr -inum 1235 -print
8 : Search in root directory for all files which have less than 2 links.
# find / -links -2 -print
9 : Search in current directory for all files whose owner is abc1 and group is grp1.
# find . \(-user abc1 -a -group grp1 \) -print
10 : Search in current directory for all files whose owner is abc1 or whose name is myfile1.
# find . \(-user abc1 -o -name myfile1 \) -print
11 : Search in current directory for all files which have permissions 777.
# find . -perm 777 -print
12 : Search in current directory for all files chose size is 10 blocks.
# find . -size 10 -print
13 : Search in current directory for all files whose size 10 bytes(characters).
# find . -size 10c -print
14 : Search in current directory for all files whose size is greater than 10 byets.
# find . -size +10c -print
15 : Search in current directory for all files which were accessed exactly 7 days back.
# find . -atime 7 -print
16 : Search in current directory for all files which have not been accessed since last 7 days (or in other words which were accessed more than 7 days ago.)
# find . -atime +7 -print
17 : Search in current directory for all files which have not been modified since last 7 days (or in other words which have been modified more than 7 days ago.)
# find . -mtime +7 -print
18 : Search in current directory for all files whose status has changed (on creation or modification ) more than 7 days ago.
# find . -ctime +7 -print
19 : Search in current directory for all files whose name is cog and instead of printing their names executes a command rm on the searched files.
# find . -name cog -exec rm {} \;
Here, the {} indicate that the searched files would become arguments for rm.The semicolon is necessary and it has to be preceded by a \ to take away its special meaning.
20 : Same as above except that this time it should ask for confirmation before executing rm command.
# find . -name cog -ok rm {} \;
Tuesday, December 8, 2015
How to configure audit to monitor file deletion in Red Hat Enterprise Linux?
Issue:
What rules can be created to monitor file deletion operation.
Solution:
Add these two entry in /etc/audit/audit.rules .
# vi /etc/audit/audit.rules
-a always,exit -F arch=b32 -S unlink -S unlinkat -S rename -S renameat -k delete
-a always,exit -F arch=b64 -S unlink -S unlinkat -S rename -S renameat -k delete
After writing the rules, restart the service auditd and make it on in to retain across reboot.
# /etc/init.d/auditd restart
# chkconfig auditd on
Now for testing create a file and delete it same time.
# touc testing
# rm -rf testing
Trace the log from below path.
# tail -f /var/log/audit/audit.log
What rules can be created to monitor file deletion operation.
Solution:
Add these two entry in /etc/audit/audit.rules .
# vi /etc/audit/audit.rules
-a always,exit -F arch=b32 -S unlink -S unlinkat -S rename -S renameat -k delete
-a always,exit -F arch=b64 -S unlink -S unlinkat -S rename -S renameat -k delete
After writing the rules, restart the service auditd and make it on in to retain across reboot.
# /etc/init.d/auditd restart
# chkconfig auditd on
Now for testing create a file and delete it same time.
# touc testing
# rm -rf testing
Trace the log from below path.
# tail -f /var/log/audit/audit.log
How to restore a deleted volume group ?
Issue:
1. Unable to find the volume group, even though all devices are present.
2. LVM metadata has been deleted.
Solution:
Always there is a backup of metadata before and after running any LVM on a PV/VG/LV. which is allways taken by LVM.
Backup location is /etc/lvm/archive/ (the copies taken before executing a command) and in /etc/lvm/backup (copies taken after executing a command).
Also you can find the backup file using vgcfgrestore command.
# vgcfgrestore --list <Volume-Group-Name>
# vgcfgrestore --list geo-vg
Ouput:
# data-vg_00_00000-16736.vg
Using the vgcfgrestore command metadata can be written back to the devices belonging to that volume Group which found from backup.
# vgcfgrestore -f /etc/lvm/archive/<file-name> <Voulme-Group-Name>
Example:
# vgcfgrestore -f /etc/lvm/archive/geo-vg_00_00000-16736.vg geo-vg
Output:
# Restored volume group geo-vg
1. Unable to find the volume group, even though all devices are present.
2. LVM metadata has been deleted.
Solution:
Always there is a backup of metadata before and after running any LVM on a PV/VG/LV. which is allways taken by LVM.
Backup location is /etc/lvm/archive/ (the copies taken before executing a command) and in /etc/lvm/backup (copies taken after executing a command).
Also you can find the backup file using vgcfgrestore command.
# vgcfgrestore --list <Volume-Group-Name>
# vgcfgrestore --list geo-vg
Ouput:
# data-vg_00_00000-16736.vg
Using the vgcfgrestore command metadata can be written back to the devices belonging to that volume Group which found from backup.
# vgcfgrestore -f /etc/lvm/archive/<file-name> <Voulme-Group-Name>
Example:
# vgcfgrestore -f /etc/lvm/archive/geo-vg_00_00000-16736.vg geo-vg
Output:
# Restored volume group geo-vg
Monday, December 7, 2015
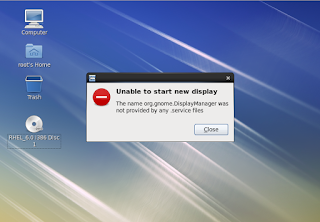
Login Error - Unable to perform switch user from GUI RHEL 6
Issue
Switch user option in the GUI interface of locked screen does not work and following error message appears:
Solution
1: Reboot the system in runlevel 5
2: Manually start the gdm using below command.
# gdm
Root Cause
1: System is running in runlevel 3.
2: Gui started using startx command, which does not initialize the display Manager
Switch user option in the GUI interface of locked screen does not work and following error message appears:
Solution
1: Reboot the system in runlevel 5
2: Manually start the gdm using below command.
# gdm
Root Cause
1: System is running in runlevel 3.
2: Gui started using startx command, which does not initialize the display Manager
Saturday, December 5, 2015
How to configure and analize Kdump in RHEL 6
Verify the kexec-tools package is installed:
# rpm -q kexec-tools
kexec-tools-2.0.0-245.el6.x86_64
If it is not installed, proceed to install it via yum:
# yum install kexec-tools
Specifying the Kdump Location
Kdump can be configured to dump directly to a device by using below mount points in /etc/kdump.conf.
# vi /etc/kdump.conf
#raw /dev/sda5
#ext4 /dev/sda3
#ext4 LABEL=/boot
#ext4 UUID=03138356-5e61-4ab3-b58e-27507ac41937
#net my.server.com:/export/tmp
#net user@my.server.com
#path /var/crash
#core_collector makedumpfile -c --message-level 1 -d 31
#core_collector cp --sparse=always
#link_delay 60
#kdump_post /var/crash/scripts/kdump-post.sh
#extra_bins /usr/bin/lftp
#disk_timeout 30
#extra_modules gfs2
#options modulename options
#default shell
Here we have configured with local partition that is /dev/sdc1.
# df -hT
Filesystem Type Size Used Avail Use% Mounted on
/dev/mapper/VolGroup-lv_root
ext4 13G 9.0G 2.8G 77% /
tmpfs tmpfs 182M 23M 160M 13% /dev/shm
/dev/sda1 ext4 485M 37M 423M 8% /boot
/dev/sdc1 ext4 5.0G 138M 4.6G 3% /kdump
Below settings will help you to configure kdump in local mounted partition as this has been done above in /kdump mount point.
# vi /etc/kdump.conf
#raw /dev/sda5
ext4 /dev/sdc1
ext4 LABEL=/kdump
ext4 UUID=03138356-5e61-4ab3-b58e-27507ac41937
#net my.server.com:/export/tmp
#net user@my.server.com
#path /var/crash
#core_collector makedumpfile -c --message-level 1 -d 31
#core_collector cp --sparse=always
#link_delay 60
#kdump_post /var/crash/scripts/kdump-post.sh
#extra_bins /usr/bin/lftp
#disk_timeout 30
#extra_modules gfs2
#options modulename options
#default shell
After the changes done then save and exit and run below two commands.
# e2lable /dev/sdc1 /kdump
# service kdump restart
So now kdump location has been configured
Testing the Configuration
Since there is no kernel panic or no issue we need to force the Linux kernel to crash, and the YYYY-MM-DD-HH:MM/vmcore file will be copied to the location you have selected in the configuration (that is, to /var/crash by default but here we have customize the path from kdump.conf).
# echo 1 > /proc/sys/kernel/sysrq
# echo c > /proc/sysrq-trigger
You need to wait for few minutes as the system will reboot and then dump file will be created
After Rebooted then you can check the YYYY-MM-DD-HH:MM/vmcore will be there.
Kdump Analyze
To analyze the vmcore dump file, you must have the crash and (kernel-debuginfo,kernel-debuginfo-common) packages installed. To install the crash package in your system, type the following at a shell prompt as root:
#yum install crash
Note that in order to use this command, you need to have access to the repository with debugging packages.
kernel-debuginfo,kernel-debuginfo-common packages only available in Redhat Repo.
Running the crash Utility
#crash /usr/lib/debug/lib/modules/`uname -r`/vmlinux /kdump/YYYY-MM-DD-HH:MM/vmcore
From crash prompt you can type below command for more analysis.
Displaying the Message Buffer
crash> log
Displaying the kernel stack trace.
crash> bt
Displaying status of processes in the system.
crash> ps
Displaying virtual memory information of the current context
crash> vm
Displaying information about open files of the current context
crash> files
Exiting the crash utility
crash> exit
# rpm -q kexec-tools
kexec-tools-2.0.0-245.el6.x86_64
If it is not installed, proceed to install it via yum:
# yum install kexec-tools
Specifying the Kdump Location
Kdump can be configured to dump directly to a device by using below mount points in /etc/kdump.conf.
# vi /etc/kdump.conf
#raw /dev/sda5
#ext4 /dev/sda3
#ext4 LABEL=/boot
#ext4 UUID=03138356-5e61-4ab3-b58e-27507ac41937
#net my.server.com:/export/tmp
#net user@my.server.com
#path /var/crash
#core_collector makedumpfile -c --message-level 1 -d 31
#core_collector cp --sparse=always
#link_delay 60
#kdump_post /var/crash/scripts/kdump-post.sh
#extra_bins /usr/bin/lftp
#disk_timeout 30
#extra_modules gfs2
#options modulename options
#default shell
Here we have configured with local partition that is /dev/sdc1.
# df -hT
Filesystem Type Size Used Avail Use% Mounted on
/dev/mapper/VolGroup-lv_root
ext4 13G 9.0G 2.8G 77% /
tmpfs tmpfs 182M 23M 160M 13% /dev/shm
/dev/sda1 ext4 485M 37M 423M 8% /boot
/dev/sdc1 ext4 5.0G 138M 4.6G 3% /kdump
Below settings will help you to configure kdump in local mounted partition as this has been done above in /kdump mount point.
# vi /etc/kdump.conf
#raw /dev/sda5
ext4 /dev/sdc1
ext4 LABEL=/kdump
ext4 UUID=03138356-5e61-4ab3-b58e-27507ac41937
#net my.server.com:/export/tmp
#net user@my.server.com
#path /var/crash
#core_collector makedumpfile -c --message-level 1 -d 31
#core_collector cp --sparse=always
#link_delay 60
#kdump_post /var/crash/scripts/kdump-post.sh
#extra_bins /usr/bin/lftp
#disk_timeout 30
#extra_modules gfs2
#options modulename options
#default shell
After the changes done then save and exit and run below two commands.
# e2lable /dev/sdc1 /kdump
# service kdump restart
So now kdump location has been configured
Testing the Configuration
Since there is no kernel panic or no issue we need to force the Linux kernel to crash, and the YYYY-MM-DD-HH:MM/vmcore file will be copied to the location you have selected in the configuration (that is, to /var/crash by default but here we have customize the path from kdump.conf).
# echo 1 > /proc/sys/kernel/sysrq
# echo c > /proc/sysrq-trigger
You need to wait for few minutes as the system will reboot and then dump file will be created
After Rebooted then you can check the YYYY-MM-DD-HH:MM/vmcore will be there.
Kdump Analyze
To analyze the vmcore dump file, you must have the crash and (kernel-debuginfo,kernel-debuginfo-common) packages installed. To install the crash package in your system, type the following at a shell prompt as root:
#yum install crash
Note that in order to use this command, you need to have access to the repository with debugging packages.
kernel-debuginfo,kernel-debuginfo-common packages only available in Redhat Repo.
Running the crash Utility
#crash /usr/lib/debug/lib/modules/`uname -r`/vmlinux /kdump/YYYY-MM-DD-HH:MM/vmcore
From crash prompt you can type below command for more analysis.
Displaying the Message Buffer
crash> log
Displaying the kernel stack trace.
crash> bt
Displaying status of processes in the system.
crash> ps
Displaying virtual memory information of the current context
crash> vm
Displaying information about open files of the current context
crash> files
Exiting the crash utility
crash> exit
Wednesday, December 2, 2015
How to disable USB storage devices on Red Hat Enterprise Linux?
Environment
- Red Hat Enterprise Linux(RHEL) 5
- Red Hat Enterprise Linux(RHEL) 6
- Red Hat Enterprise Linux(RHEL) 7
Solution:
Add the following line in the file/etc/modprobe.d/blacklist.confblacklist usb-storageNote: blacklist.conf file exists in RHEL 5 and 6 environments, but will be created by this method in RHEL 7.
Subscribe to:
Comments (Atom)